
?
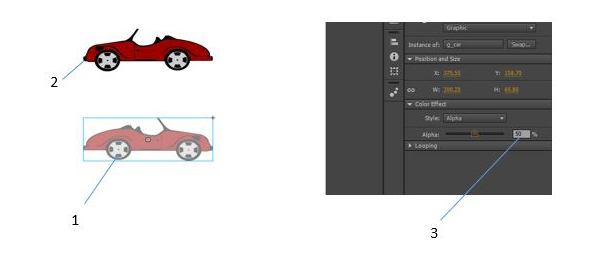
Item 1 in the figure above is an example of a(n) ___________.
Fill in the blank(s) with the appropriate word(s).
button
You might also like to view...
This attack uses a spoofing technique to carry out the attack. The attacker spoofs the victim’s IP address and sends requests many different servers or devices that respond to that type of re-quest. The devices all then reply back to the victim’s IP address, which is unable to process the overwhelming amount of traffic.
What will be an ideal response?
Which of the following can be used to increase the visibility of your website?
A. A site map B. A social networking site C. An SSL certificate D. An HTTPS server
Answer the following statement true (T) or false (F)
SQL stands for Syntactical Question Language.
Answer the following statement true (T) or false (F)