Chinese hackers whose stated goal is to infiltrate Western computer systems are called the ___________
a. Eastern Alliance
b. China Eagle Union
c. Shanghai Express
d. None of the above
Answer B.
You might also like to view...
Clusters of documents can be summarized by finding the top terms (words) for the documents in the cluster, e.g., by taking the most frequent k terms, where k is a constant, say 10, or by taking all terms that occur more fre- quently than a specified threshold. Suppose that K-means is used to find clusters of both documents and words for a document data set.
(a) How might a set of term clusters defined by the top terms in a document cluster differ from the word clusters found by clustering the terms with K-means? (b) How could term clustering be used to define clusters of documents?
Under which of the following security models are users allowed access only to information that is not considered to be in conflict with other information that they already possess?
A) Biba Integrity Model B) Clark-Wilson Model C) Chinese Wall Model D) Bell-LaPadula Model
What statuses are listed?
What will be an ideal response?
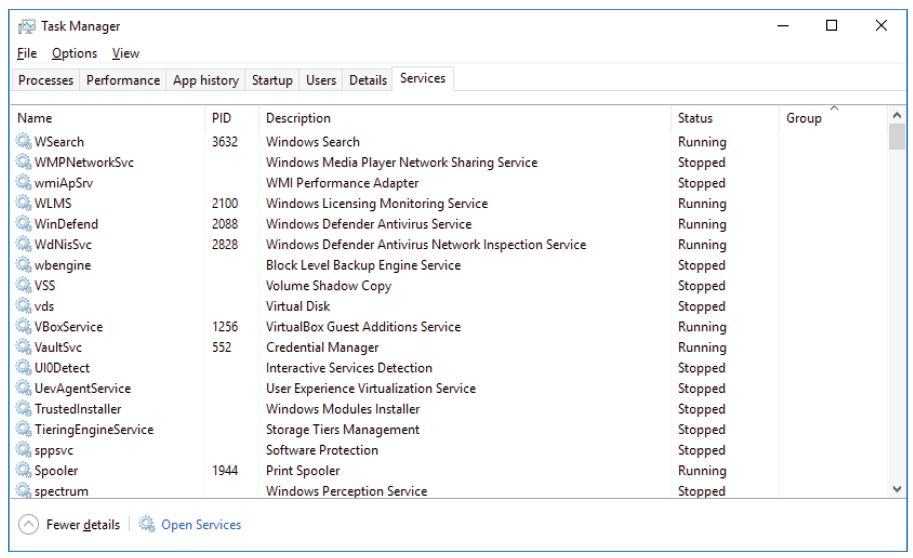
Open Task Manager: Right-click the Task bar to open Task Manager.
Working in the Services Tab
a. Click the Services tab. Use the scroll bar on the right side of the Services window to view all the services listed.
Which of the following virus scanners runs only when the user launches it?
a. On-demand virus scanner b. Ongoing virus scanner c. Constant virus scanner d. None of the above