List five disaster recovery safeguards that can be used to help guarantee a relatively quick and painless recovery in the event that a disaster occurs.
What will be an ideal response?
Maintain up-to-date off-site backups.
Use uninterruptable power sources on critical systems.
Maintain an inventory of spare components.
Keep up to date on all software updates.
Secure and monitor all equipment adequately.
Restrict access to sensitive equipment.
Use fiber for external building-to-building connections instead of copper wire.
Convince those in administration (or purchasing) that there are no corners that can be cut when planning for disaster recovery.
You might also like to view...
Write an application that displays a solid square com- posed of a character input by the user (Fig. 12.29). The user also should input the size of the side of the square.
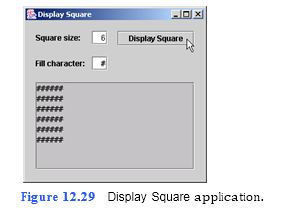
a) Copying the template to your working directory. Copy the C:Examples Tutorial12ExercisesDisplaySquare directory to your C:SimplyJava direc- tory.
b) Opening the template file. Open the DisplaySquare.java file in your text editor.
c) Adding a method to your application that displays a square of characters. On line
141, add a comment indicating that the method will display a square in a JTextArea. On line 142, add the method header for this method. The method will be called dis- playSquare. This method contains two parameters–the first, of type int, should be called size, the second, of type String, should be called character. This method does not return a value, but simply performs a task (displaying a square). For such methods, the return type is specified as void. Specify the return type for display- Square as void. On line 143, add a left brace to begin the body of the method. On line 145, add the right brace to end the body of the method. Follow the brace with a comment i
Which statement is false?
a. The shape of a binary search tree that corresponds to a set of data can vary, depending on the order in which the values are inserted into the tree. b. A node can be inserted at any point in a binary search tree. c. The process of creating a binary search tree actually sorts the data, and thus this process is called the binary tree sort. d. The binary search tree facilitates duplicate elimination.
The Internet Protocol (IP) primarily works to transmit and deliver data between devices on internetworks.
Answer the following statement true (T) or false (F)
Answer the following statement(s) true (T) or false (F)
Magnet AXIOM Cloud can retrieve information from Skype, Instagram, Twitter, iCloud, but not from Facebook Messenger.