What are people-intensive verification techniques that are conducted either formally or informally that allow peers to read code statements and look for common security vulnerabilities, such as hard-coded IDs or passwords,and general quality features?
A. Code scanners
B. Code Reviews
C. Load testers
D. Fuzzing
Answer: B
Computer Science & Information Technology
You might also like to view...
The frame rate for the PAL system is _____ fps.
A. 24 B. 25 C. 28.9 D. 29.97 E. 30
Computer Science & Information Technology
In Windows 10, ____________________ provides both antivirus and antispyware capabilities.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
On a chart, ________ can be used to point out items that need more explanation
A) callouts B) values C) a legend D) perspective
Computer Science & Information Technology
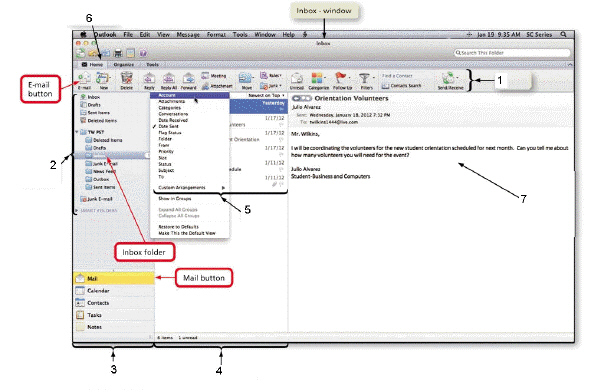 The item numbered 3 in the accompanying figure can be used to browse Outlook folders using all of the following views EXCEPT ____.
The item numbered 3 in the accompanying figure can be used to browse Outlook folders using all of the following views EXCEPT ____.
A. Mail B. Messages C. Contacts D. Tasks
Computer Science & Information Technology