Which protocol is used to remotely access the whole desktop of another computer?
A. Telnet
B. Secure Shell
C. Virtual Network Computing (VNC)
D. HyperText Transfer Protocol (HTTP)
Answer: C
You might also like to view...
To assign an access key to a text box control, you include the ____ in the Text property of the control's identifying label.
A. exclamation mark B. ampersand C. asterisk D. caret
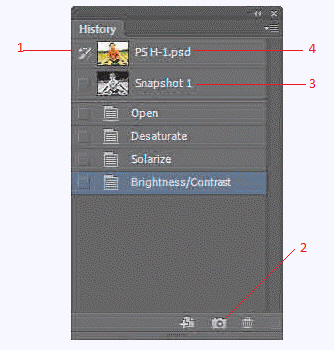 In the accompanying figure, which number represents the default thumbnail image?
In the accompanying figure, which number represents the default thumbnail image?
A. 1 B. 2 C. 3 D. 4
After you enter and save contact information, that information is available as you compose ____________________.
Fill in the blank(s) with the appropriate word(s).
Case Based Critical ThinkingKatie was promoted to senior designer because of her extensive knowledge of color theory and working with CMYK color for printing. Now, her challenge is to pass that knowledge on to her staff. Katie's team is working on a 2-color job, which consists of Black and PMS 185 inks that will print on an offset printing press. When the client changes the color ink to PMS 186 ____.
A. Katie must go through the document and find and change all objects and text colored with PMS 185. B. Katie doesn't need to make the change because the two inks are so close in color. C. Katie can replace PMS 185 with PMS 186 in the file quickly - it's no big deal.