Which type of individual may steal credit card numbers to make fraudulent purchases?
A. corrupt
B. Caesar
C. administrator
D. kiddie
Answer: A
You might also like to view...
Which of the following would most likely be classified as confidential information under the private sector classification system?
A) Laboratory research B) Social Security number C) List of upcoming trade shows D) Nonsensitive client or vendor information
The Convert Shape command is found on the ____.
A. Object menu B. Shape menu C. Tools menu D. Edit menu
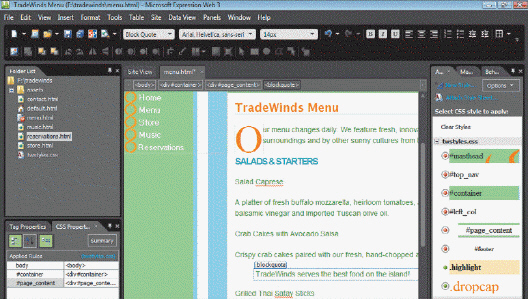 Referring to the figure above, the quote "Tradewinds serves the best food on the island!" in the middle of the page has a
Referring to the figure above, the quote "Tradewinds serves the best food on the island!" in the middle of the page has a
tag. To add this tag, you should click in the chosen text, click ____, then click Block Quote.A. the Style list arrow on the Common toolbar B. the Style list arrow on the Menu bar C. Edit on the Menu bar, followed by Quote Type on the Submenu D. Format on the Common toolbar, followed by Style on the Submenu
To view the underlying XML of an RSS feed, right-click in the browser window and select View Source or ____________________.
Fill in the blank(s) with the appropriate word(s).