A(n) _________ is a piece of malware that, by definition, gains privileged access to a computer.
Fill in the blank(s) with the appropriate word(s).
rootkit
correct
Computer Science & Information Technology
You might also like to view...
Terminal operations are ________; they perform the requested operation when they are called.
a. immediate b. idle c. lazy d. eager
Computer Science & Information Technology
Discuss whether the following operations are idempotent: i) Pressing a lift (elevator) request button; ii) Writing data to a file; iii) Appending data to a file. Is it a necessary condition for idempotence that the operation should not be associated with any state?
What will be an ideal response?
Computer Science & Information Technology
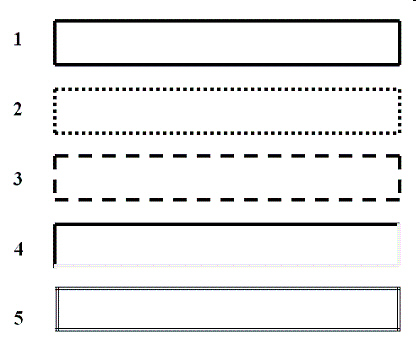 The item marked 5 in the accompanying figure is an example of the ____ style.
The item marked 5 in the accompanying figure is an example of the ____ style.
A. dotted B. double C. dashed D. inset
Computer Science & Information Technology
Any major navigation blocks should be placed inside the ____ element.
A.
Computer Science & Information Technology