The sh ip route command is entered on RouterB in the campus LAN shown in Figure 9-18. The LAN has been fully configured to run EIGRP. How many EIGRP subnets are running on the network? Identify the connected C and EIGRP D subnets.
Figure 9-18
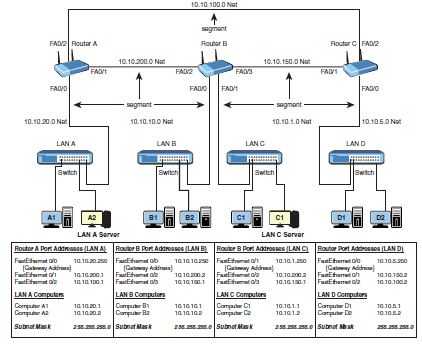
7 subnets
See below:
RouterB#sh ip route
Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B -
BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, * - candidate
default
U - per-user static route, o - ODR
T - traffic engineered route
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 7 subnets
D 10.10.5.0 [90/2195456] via 10.10.150.2, 00:01:03, Ethernet3
C 10.10.10.0 is directly connected, Ethernet0
C 10.10.1.0 is directly connected, Ethernet1
D 10.10.20.0 [90/2195456] via 10.10.200.1, 00:01:02, Ethernet2
D 10.10.100.0 [90/2681856] via 10.10.200.1, 00:01:03, Ethernet2
[90/2681856] via 10.10.150.2, 00:01:03, Ethernet3
C 10.10.150.0 is directly connected, Ethernet3
C 10.10.200.0 is directly connected, Ethernet2
You might also like to view...
Once data items are stored using a database management system, applications may be written in ____________ to communicate with the DBMS.
a. Java b. C# c. Visual Basic d. any of these
List two reasons IPsec has become the standard set of protocols for VPN security.
What will be an ideal response?
To select the ROUND function, you click the ________ button in the Function Library group on the Formulas tab
A) Trig B) Statistics C) Math & Trig D) Math & Statistics
This function checks whether criteria are met and returns one value if TRUE and another value if
FALSE. A) TRUE B) IF C) BRANCH