_____ is a program in which malicious code is hidden inside a seemingly harmless program.
a. A Trojan horse
b. A distributed denial-of-service attack
c. A spam
d. A smish
a. A Trojan horse
A Trojan horse is a program in which malicious code is hidden inside a seeminglyharmless program. The program’s harmful payload might be designed to enable the hacker to destroy hard drives, corrupt files, control the computer remotely, launch attacks against other computers, steal passwords or Social Security numbers, or spy on users by recording keystrokes and transmitting them to a server operated by a third party.
You might also like to view...
This is a control structure that causes a statement or group of statements to repeat.
a. decision statement b. loop c. cout object d. selection structure e. None of these
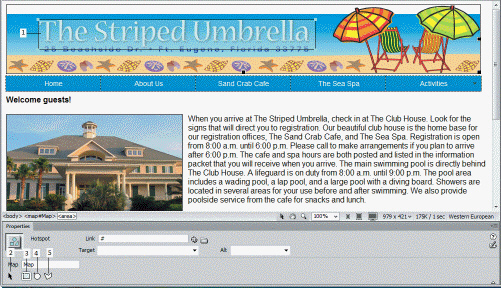 In the accompanying figure, Item 2 refers to the ____.
In the accompanying figure, Item 2 refers to the ____.
A. outline of the hotspot B. Pointer Hotspot tool C. Rectangle Hotspot tool D. Polygon Hotspot tool
When planning a new form, you should decide how the data will be collected and interpreted by selecting a(n) ____________________.
Fill in the blank(s) with the appropriate word(s).
If records in one table are associated with records in another table they have a __________.
a. Key b. Relationship c. View d. Linking table