One form of e-mail attack that is also a DoS attack is called a mail spoof, in which an attacker overwhelms the receiver with excessive quantities of e-mail. __________
Answer the following statement true (T) or false (F)
False
You might also like to view...
Why can’t binary data be represented directly in XML, for example, by representing it as Unicode byte values? XML elements can carry strings represented as base64. Discuss the advantages or disadvantages of using this method to represent binary data.
What will be an ideal response?
In JDK 1.5, you may directly assign a primitive data type value to a wrapper object. This is called ______________.
a. auto boxing b. auto unboxing c. auto conversion d. auto casting
You can fill a path with a ____ and outline it with a line.
A. color B. pattern C. gradient D. any of the above
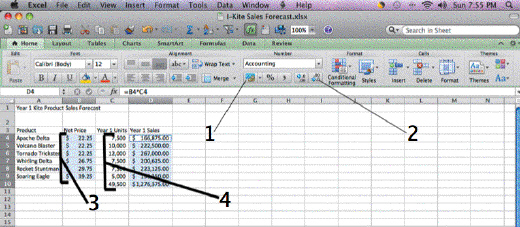 In the accompanying figure Item 4 points to values formatted with ____ and no decimals.
In the accompanying figure Item 4 points to values formatted with ____ and no decimals.
A. currency B. fraction C. comma D. number