Jane has left the company. Her user account is a member of several groups and has permissions and rights to a number of forest-wide resources. Jane's replacement will arrive in a couple of weeks and needs access to the same resources. What's the best course of action?
a: Find all groups Jane is a member of and make note of the,. Delete Jane's user account and create a new account for the new employee. Add the new account to all the groups Jane was a member of.
b: Copy Jane's user account and give the copy another name.
c: Disable Jane's account. When the new employeee arrives, rename Jane's account, assign it a new password and enable it again.
d: Export Jane's account and then import it when the new employee arrives. Rena,e the account and assign it a new password.
c: Disable Jane's account. When the new employeee arrives, rename Jane's account, assign it a new password and enable it again.
You might also like to view...
Case-Based Critical Thinking QuestionsCase 9-1Kyra is preparing speaker notes and handouts for her presentation. Please answer the questions below.Kyra notices that several of the slides do not contain notes. Kyra will click the ____ view button to display speaker notes, and will add them to the slides where notes are missing.
A. Slide Show B. Presenter C. Print D. Normal
?In the accompanying image of Microsoft PowerPoint 2016, Box A points to the _____ placeholder.
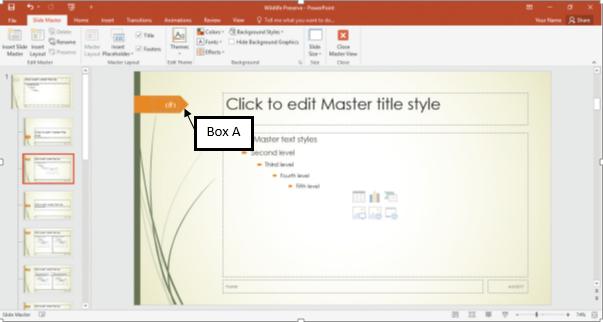
A. ?Date B. ?Title C. ?Header and Footer D. ?Slide Number
The shape of a video can be edited in PowerPoint 2010
Indicate whether the statement is true or false
What is the role of context in MobileApp design?
What will be an ideal response?