A(n) ________________ takes place when an unauthorized person gains access to a digital device by using an Internet connection and exploiting vulnerabilities in hardware or software.
A. address spoofing exploit
B. online intrusion
C. brute force attack
D. rogue antivirus
Answer: B
You might also like to view...
The ____________________ professional is a specialist in physical security.
Fill in the blank(s) with the appropriate word(s).
When an element is added to a queue, it is added to the rear. When an element is removed, it is removed from the
A) rear. B) middle. C) front. D) All of the above E) None of the above A
?Which of the following laws covers false claims regarding unauthorized use of credit cards?
A. ?Computer Fraud and Abuse Act B. ?Fraud and Related Activity in Connection with Access Devices Statute C. Identity Theft and Assumption Deterrence Act D. Stored Wire and Electronic Communications and Transactional Records Access Statutes
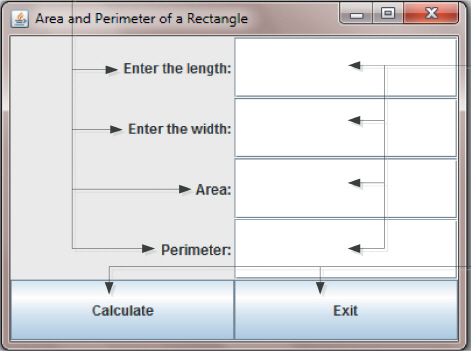 Which of the following from the window above is a JButton?
Which of the following from the window above is a JButton?
A. Calculate B. Exit C. Both Calculate and Exit D. Perimeter