Discuss the policy sets that an organization might consider when planning fine-grained password policies.
What will be an ideal response?
When your organization plans fine-grained password policies, it is typical to consider having at least three basic policy sets: one for ordinary users, one for administrators, and one for service accounts (such as accounts used by programs that need access to the server). In many cases you can use global administrator and user groups you have already created as the global shadow security groups-there is no need to make life more complicated by adding more groups. Next, consider adding more fine-grained password policies as new security needs arise. For example, you may need to create a set of policies for company auditors because they are given extensive access to the financial resources contained in an accounting server.
You might also like to view...
The hierarchical tree structure stored in memory by the XML parser is called the ________.
a) Document Type Definition (DTD) b) Simple Object Access Protocol (SOAP) c) Active Server Page (ASP) d) Document Object Model (DOM)
To declare a class as abstract, you use the ____________ in the class header.
a. void keyword b. new keyword c. abstract keyword d. static keyword
(Challenge) you went to a video store and rented a DVD that is due in 3 days from the rental date. Input rental date, rental month and rental year. Caclculate and print return date, return month and return year.
For example,
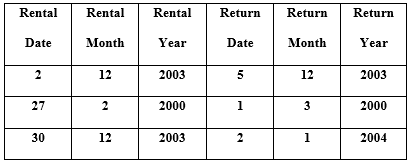
What is "6to4"?
What will be an ideal response?