?Software forensics tools are grouped into command-line applications and GUI applications
Answer the following statement true (T) or false (F)
True
You might also like to view...
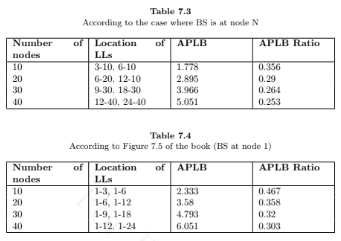
In a string topology SWWSN with one LL, prove that the optimal LL addition for achieving minimal APLB is made between the BS and the node at fractional location 0.6.
Where do you look in a packet captured by Wireshark to find the encrypted version of the username and password when the TLS protocol is in use?
A. Secure Sockets Layer B. TTL C. Transmission Control Protocol D. TCP Analysis Flags
OLE DB relies on connection strings that enable the application to access the data stored on an external device.
Answer the following statement true (T) or false (F)
The Twirl filter in the ____________________ category creates a circular effect in an image.
Fill in the blank(s) with the appropriate word(s).