Although the _________ attack is a serious threat, there are simple countermeasures that can be used such as constant time calcs, random delays or blinding computations.
A. timing B. chosen ciphertext
C. mathematical D. none of the above
A. timing
Computer Science & Information Technology
You might also like to view...
What is a point-to-point network?
What will be an ideal response?
Computer Science & Information Technology
Use the SQL _____________ keyword to perform regular expression matching.
a. LIKE b. REGEXP c. POSIX d. IS NULL
Computer Science & Information Technology
Which statement is false?
a. Interface JdbcRowSet is in the javax.rowset package. b. A CachedRowSet object is scrollable and updatable by default. c. A JdbcRowSet object is scrollable and updatable by default. d. JdbcRowSet is a connected RowSet.
Computer Science & Information Technology
FIGURE 9-1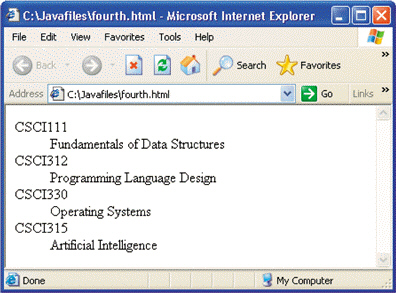 Figure 9-1 above shows an example of a(n) ____ list.
Figure 9-1 above shows an example of a(n) ____ list.
A. ordered B. unordered C. definition D. nested
Computer Science & Information Technology