Which of the following are implemented to ensure that an organization can control mobile device settings, applications, and other parameters when they are attached to the enterprise? (Choose two.)
A. APT
B. CERT
C. MDM
D. MAM
C,D
Explanation: Mobile device management (MDM) and mobile application management (MAM) tools are implemented to ensure that an organization can control mobile device settings, applications, and other parameters when they are attached to the enterprise.
You might also like to view...
As shown in the accompanying figure, the red rectangle that appears at the top of the Timeline above the currently displayed frame is the ____________________.
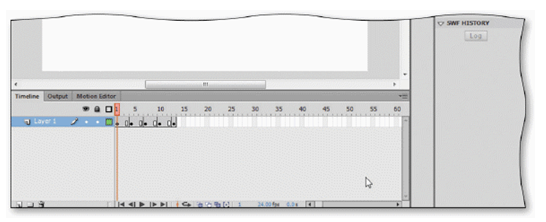
Fill in the blank(s) with the appropriate word(s).
Which of the following statements is false?
a. Assigning a value to a nonexistent key inserts the key–value pair in the dic-tionary. b. String keys are case insensitive. c. Assigning a value to a nonexistent key could be a logic error. d. All of the above statements are true.
If the sort pattern split routine consistently splits the array into two pieces size 1 and another of size N-1 then the run time is”
a) O(N2) b) O(log N) c) O(N1/2) d) O(N log N) e) The run-time depends on too many things to answer this.
Describe an advantage of having a multiuser system.
What will be an ideal response?