With ______________ iteration the library determines how to access all the elements in a col- lection to perform a task.
What will be an ideal response?
internal.
You might also like to view...
Because ____ files are supported by virtually all paint, image-editing, and page-layout applications, it is a versatile format for cross-platform applications.
a. PDF b. JPG c. BMP d. TIF
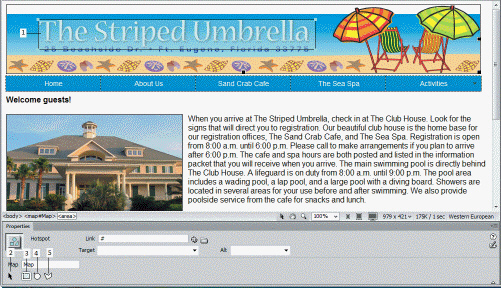 In the accompanying figure, Item ____ is the Pointer Hotspot tool.
In the accompanying figure, Item ____ is the Pointer Hotspot tool.
A. 2 B. 3 C. 4 D. 5
The ________ function finds the lowest value in a list
Fill in the blank(s) with correct word
Which of the following scenarios best describes the compromise of confidential data regarding organizational plans, products, or services?
a. Fire destroys all the physical assets in an organization. b. Employees use corporate email to disseminate sexually explicit material. c. Senior executive loses laptop containing critical data. d. Employees waste time at work visiting Web sites unrelated to their work.