An administrator notes that after a recent power outage, some open files were corrupted on one affected file server. Which of the following items should the administrator consider to determine the cause of this corruption?
A. The servers memory
B. The servers RAID controller battery
C. The servers processor
D. The servers NIC teaming configuration
Answer: B. The servers RAID controller battery
You might also like to view...
When you define a variable, you provide Alice with a(n) ____.
A. parameter, navigator, and property B. instance, initial statement, and return value C. name, type, and initial value D. declaration, initializer, and expression
Today’s ________ computers, smartphones and tablets enable computers to perform tasks truly concurrently.
a) large memory b) multiscreen c) soft keyboard d) multicore
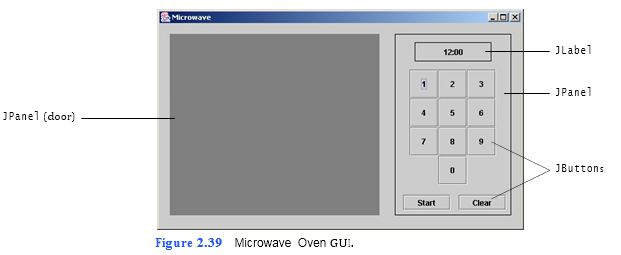
(Microwave Oven GUI) JPanels, like other GUI components, have bounds and back- ground properties. In this exercise, you will customize the bounds and background properties of the JPanel that represents a microwave oven’s door. The completed GUI is shown in Fig. 2.39.
a) Copying the template to your working directory. Copy the C:Examples Tutorial02ExercisesMicrowaveOven directory to your C:SimplyJava directory.
b) Opening the Command Prompt window and changing directories. Open the Com- mand Prompt by selecting Start > Programs > Accessories > Command Prompt. Change to your working directory by typing cd C:SimplyJavaMicrowaveOven, then pressing Enter.
c) Compiling the template application. Compile your application by typing the com- mand javac Microwave.java, then pressing Enter.
d) Running the template application. Run the application by typing java Microwave- Oven. The GUI of the Microwave template application should appear as shown in Fig. 2.40.

e) Closing the application. Close the running application by clicking its close button.
This returns you to th
In one of the HNV address spaces, the ________ refers to either the information technology group within a company-owned private cloud, or it can refer to a hosting organization that manages a public cloud containing one or more customers or tenants
a. Provider b. Customer c. Web site d. None of the above