Within security perimeters the organization can establish security redundancies, each with differing levels of security, between which traffic must be screened. _________________________
Answer the following statement true (T) or false (F)
False
You might also like to view...
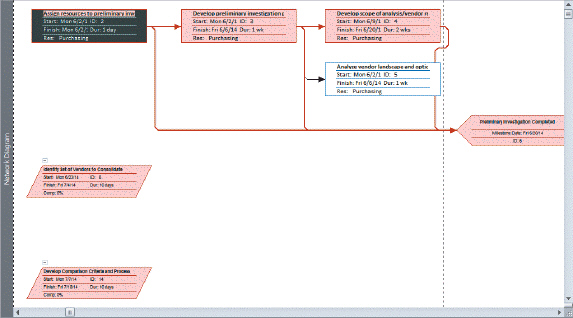 The selected task in the accompanying figure is ____.
The selected task in the accompanying figure is ____.
A. Assign resources to preliminary investors B. Develop preliminary investigation C. Analyze vendor landscape and options D. Preliminary Investigation Completed
The status of protocol up indicates which of the following? (Select all that apply.)
A) The Ethernet interface is connected to another networking device. B) Keepalive packets are being exchanged. C) The routing protocol has been configured. D) The router is ready to be configured.
Why would making a modification, such as changing the order of steps, to a flowchart be easier than making the same modification to pseudocode? Explain your answer.
What will be an ideal response?
A(n) _______________ is the specific interactive occurrence that triggers the action of a button created in InDesign.
Fill in the blank(s) with the appropriate word(s).