CSS3 added support for the HSL system, which enables you to create colors by specifying values or percentages for hue, ____, and light.
A. settings
B. saturation
C. shading
D. shadows
Answer: B
You might also like to view...
A security engineer is using a sniffer to determine the source of apparently hostile traffic on an organization’s internal routed network. When the engineer examines individual frames, he sees that the source MAC address for the hostile packets matches the MAC address for the router on the local network. What is the best explanation for this?
a. The packets are encapsulated in a tunneling protocol such as PPTP. b. The packets have a spoofed originating MAC address in order to make identification of the hostile node more difficult. c. Frames carrying IP traffic originating on another network will have a MAC address for the local network’s router. d. The packets are IPX protocol, not IP.
Configure the network according to the specifications listed. Make sure that you address both the internal and external access rules. Test your network carefully and then save your configuration. You will be asked to demonstrate your network to your instructor for grading. Make sure the ping command operates properly and the access rules are being implemented as specified in the requirements.
The objective of this project is for the students to gain experience configuring VLANs and access
lists for controlling data traffic into and out of the VLANs and the wide-area network connection.
This network setup has two separate sites, Site A and Site B, that are connected through Routers 1
and 2. The network address for Site A is 172.168.0.0. The network address for Site B is
192.168.35.0. IP addressing and subnetting within your network is up to you; however, plan your
network carefully.
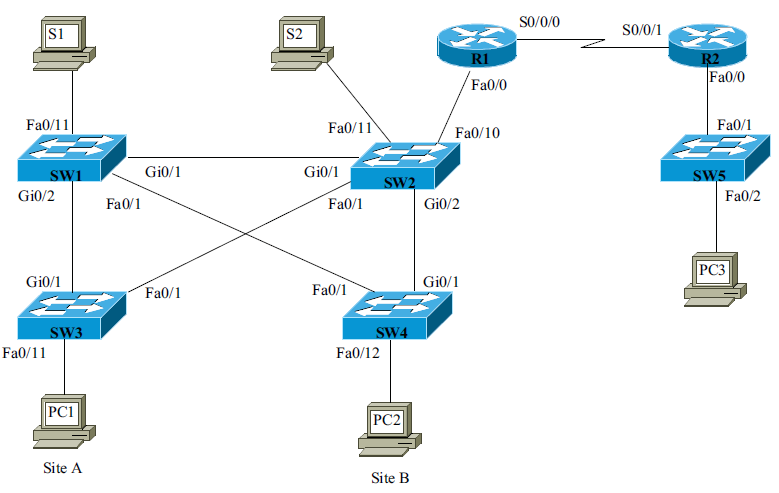
Specifics
Site A:
? Research VLAN (PC1), server (S1)
? Finance VLAN (PC2), server (S2)
Site B:
? Office LAN (PC3)
Internal access rules:
? Computers on the Office and Finance VLANs can communicate with the server (S2).
? Only the computers in the Research VLAN can talk to the Research server (S1).
External access rules:
? Only the computers in the Office and Finance LANs can access the wide-area network conne
Describe the twisted nematic (TN) technology.
What will be an ideal response?
Using source port numbers as a way to keep track of connections is a characteristic of which of the following protocols?
A. TCP B. UDP C. NAT D. PAT