With implementation hiding, when you make a request to a method, you only know the details of how the method is executed.
Answer the following statement true (T) or false (F)
False
You might also like to view...
________ and WPA are wireless security protocols which use encryption to secure wi_fi networks
Fill in the blank(s) with correct word
Create an application that mimics the functionality of a vending machine. Your application’s GUI has been completed for you (Fig. 14.18). Store the prices of each item for sale in the vending machine in an instance variable. Also, add the code that will display the price of an item when the item’s number has been entered and Enter JButton has been clicked.
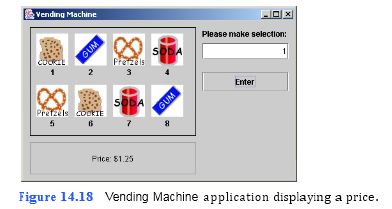
a) Copying the template to your working directory. Copy the C:Exam- plesTutorial14ExercisesVendingMachine2 directory to your C:SimplyJava directory.
b) Opening the template file. Open the VendingMachine.java file in your text editor. c) Adding instance variables. After the last GUI component is declared (line 53),
declare private String instance variables to store the prices of each of the snacks.
Each String should be in the form "$0.00" where the price of the snack is substi- tuted for the zeros. The variables’ names and prices should be snackPrice1 ("$1.25"), snackPrice2 ("$0.50"), snackPrice3 ("$1.25"), snackPrice4 ("$1.00"), snackPrice5 ("$1.25"), snackPrice6 ("$1.25"), snackPrice7 ("$1.00") and snackPrice8 ("$0.50").
d) Coding the enterJButtonActionPerformed method. Locate the enterJButtonAc- tionPerformed method. In this method, store the user input entered in the inputJ- TextField. Then, use a switch statement to di
A ____ is used to mount a file system in another location and have it accessible from both locations.
A. runlevel link B. bindmount target C. forwarder D. map
To open the Print dialog box, click the Print command on the ____________________ menu.
Fill in the blank(s) with the appropriate word(s).