The stage of the plan-protect response cycle that consumes the most time is ________.
A. hacking
B. response
C. protection
D. planning
C. protection
Computer Science & Information Technology
You might also like to view...
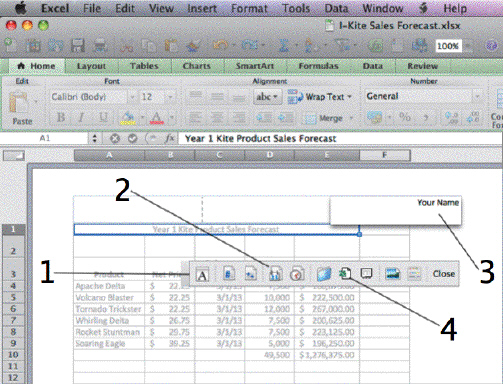 In the accompanying figure, Item 1 points to the ____.
In the accompanying figure, Item 1 points to the ____.
A. Format floating toolbar B. Formula floating toolbar C. Worksheet floating toolbar D. Header and Footer floating toolbar
Computer Science & Information Technology
Select the attribute used to limit the number of characters that a text box will accept
a. size b. maxlength c. limit d. columns
Computer Science & Information Technology
What utility would a technician use to see what stop error was displayed briefly before the computer rebooted?
A) Task Manager B) MSCONFIG C) Event Viewer D) DXDIAG
Computer Science & Information Technology
When you add a new field to a form, two controls are usually created: a caption and a text box. _________________________
Answer the following statement true (T) or false (F)
Computer Science & Information Technology