Buffer overflow attacks have become less prevalent with the growth of the Internet.
Answer the following statement true (T) or false (F)
False
You might also like to view...
Which of the following statements is false?
a. Lambda expressions can be used anywhere functional interfaces are expected. b. A lambda consists of a parameter list followed by the arrow token and a body, as in: [parameterList] -> {statements} c.Method references are specialized shorthand forms of lambdas. d. Each of the above statements is true.
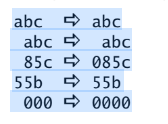
Write a sed command that copies a file to standard output, replacing a sin- gle SPACE as the first character on a line with a 0 (zero) only if the SPACE is immediately followed by a number (0–9). For example:
A field that uniquely identifies each record in a table is called the ________
A) primary key B) datasheet C) criterion D) foreign key
You have been awarded a contract for wiring a new federal building. What twisted-pair wiring standard must you use?
a. TIA/EIA 568A b. TIA/EIA 568B c. TIA/EIA 568F d. TIA/EIA rollover