Samantha is having an issue with Windows crashing and believes that malicious software is causing it to crash. Samantha also has received application errors that have cause the applications to close.
Which event log in the Event Viewer can Samantha inspect to see if malicious software is causing the Windows system to crash and the application errors, system errors, and other types of errors?
A. System logs
B. Security logs
C. Setup logs
D. Application
Answer: A
You might also like to view...
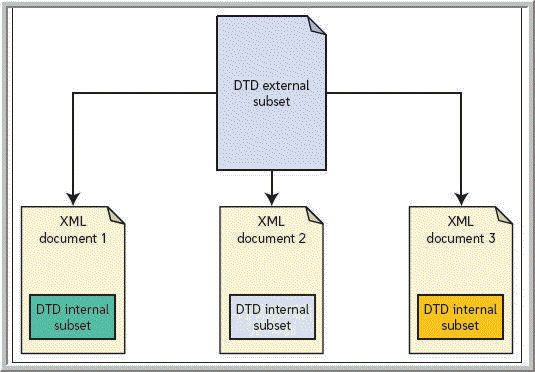 The locations of external subsets like that shown in the accompanying figure can be defined using ____ types of identifiers.
The locations of external subsets like that shown in the accompanying figure can be defined using ____ types of identifiers.
A. two B. three C. four D. six
Give the sequence of steps for creating and using a dynamic array.
What will be an ideal response?
Sara, a user, receives a call and the caller asks if Sara would be willing to answer a few marketing questions, and in return be placed in the drawing to win a trip to Hawaii. After Sara agrees, she is transferred to an automated service which states that some personal information needs to be collected to verify her full name, birthday, address, and email to be eligible for the Hawaii trip. After providing the details Sara is then solicited for banking preferences, general purchasing preferences, and debit card details. Which of the following BEST describes this type of attack?
A. A hoax B. Pharming C. Smurfing D. Vishing
There are no countermeasures for SNMP enumeration.
a. true b. false