Which of the following often requires kerning?
A. Large blocks of text
B. Headlines
C. Footnotes
D. Numbers
Answer: B
Computer Science & Information Technology
You might also like to view...
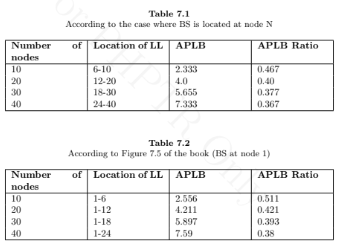
For the above problem, estimate the APLB reduction factor due to the transformation to an SWWSN. What is the impact on APLB when you add one more LL to the SWWSN between locations 0 . 3 N and BS?
Computer Science & Information Technology
Newer Trojans listen at a predetermined port on the target computer so that detection is more difficult.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
What is the term used when an IDPS doesn't recognize that an attack is underway?
A. false negative B. true positive C. negative activity D. positive signature
Computer Science & Information Technology
PivotTables in Access are a view option for the data source that is opened, which means they are not independently created
Indicate whether the statement is true or false
Computer Science & Information Technology