You can add generated content using the:beforeand __________ pseudo-elements.
Fill in the blank(s) with the appropriate word(s).
after
Computer Science & Information Technology
You might also like to view...
In order for a defense to be effective, all of the requisite ____ have to be in place and properly coordinated.
A. assets B. intrusions C. countermeasures D. backup controls
Computer Science & Information Technology
Write a sed command that copies a file to standard output, replacing a sin- gle SPACE as the first character on a line with a 0 (zero) only if the SPACE is immediately followed by a number (0–9). For example:
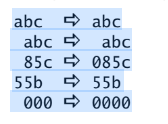
Computer Science & Information Technology
The ________ loops through an object collection or an array
A) Do…While loop B) Do…Until loop C) For loop D) For…Each loop
Computer Science & Information Technology
Using digit extraction selected digits are extracted from the key and used as the address.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology