It is best to group your Sub procedures together by what they do into separate modules, renaming the module appropriately to describe the kind of procedures it contains
Indicate whether the statement is true or false
TRUE
You might also like to view...
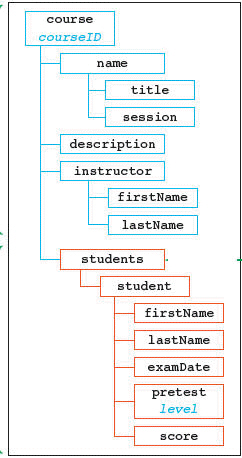 In the accompanying figure, an example of an element from the students vocabulary is _______.
In the accompanying figure, an example of an element from the students vocabulary is _______.
A. firstName B. student C. instructor D. name
________ is the process of systematically selecting representative elements of a population.
A) Questioning B) Calling C) Sampling D) Learning
Management at your company has become increasingly concerned about botnet attacks. After researching the issue, you decide to monitor certain conditions to help detect if a botnet attack is underway. Which trend is the best indicator of this type of attack?
A. connection attempt increase on Internet-facing Web servers B. TCP and UDP traffic increase during off-peak hours C. port-scanning attempt increase over a 24-hour period D. unsuccessful login increase during peak hours
When a node is created, it is added to the computer memory as a _________ by appending it to a node within a tree.
Fill in the blank(s) with the appropriate word(s).