Describe the default behavior of Windows Firewall.
What will be an ideal response?
By default, Windows Firewall blocks all incoming IP packets that attempt to initiate a session.
You might also like to view...
After you have completed essential steps following a security breach and have notified the appropriate people, what should be the final step?
A) Copy the logs of all affected systems for use as evidence. B) Perform an emergency audit to determine whatdamage has been done. C) Meet with IT staff to discuss what can be learned and how to prevent it from happening again. D) Change all affected passwords and repair any damage that has been done.
To remove a text-shadow, set the value of the text-shadow style to ____.
A. 0 B. none C. 1 D. empty
After choosing a shape tool from the Tools panel, use the ____ button at the bottom of the Tools panel in the accompanying figure to select the drawing mode.
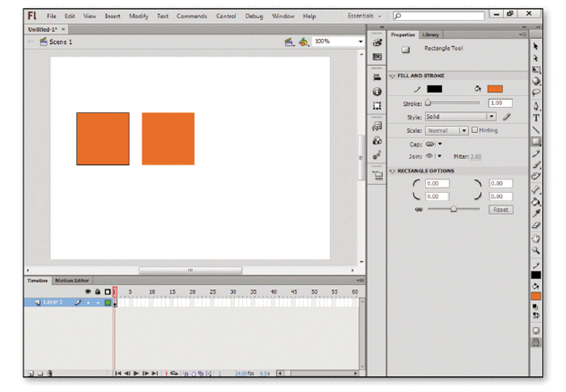
a. Creation
b. Shape
c. Object Drawing
d. Illustration
What would the output from the following be:
``` int x = 3 0 ; for ( int i=x ; i < 4 0 ; i++) { i f ( i < 35) System . out . p r i n t l n ( " i i s l e s s than 35" ) ; el se i f ( i == 35) System . out . p r i n t l n ( " i i s 35" ) ; el se System . out . p r i n t l n ( " i i s g r e a t e r than 35" ) ; } ```