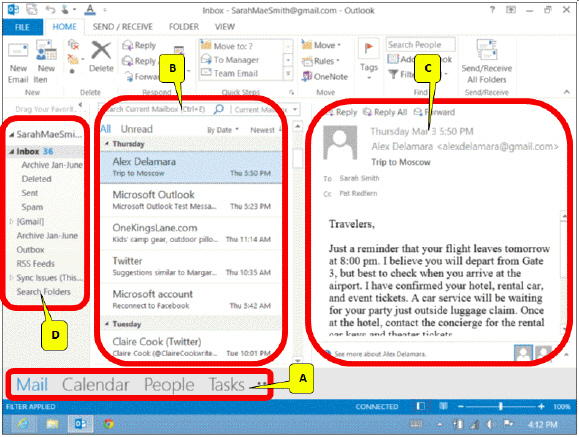
 What of the following is missing in the accompanying figure?
What of the following is missing in the accompanying figure?
A. Compose message panel
B. Ribbon bar
C. Inbox list
D. Reading panel
Answer: A
You might also like to view...
In a(n) __________ situation, a wireless device is configured to appear to be a legitimate access point, enabling the operator to steal passwords from legitimate users and then penetrate a wired network through a legitimate wireless access point.
A. malicious association B. identiy theft C. network injection D. ad hoc network
Which layer of the TCP/IP model processes requests from hosts to ensure that a connection is made to the appropriate port?
a. Application b. Internet c. Transport d. None of these answers is correct
The easiest way to pin is to install the Pin It button onto your desktop and then click that button when you find an item you want to pin
Indicate whether the statement is true or false
A(n) ____ provides a pictorial representation of an algorithm using specifically defined shapes.
A. pseudocode B. formula C. opcode D. flowchart