A computer that requests the services of a server is best known as a:
A) user B) customer C) patron D) client
D
You might also like to view...
Select the item below that does not belong in a consistent web site design.
a. the same fonts on each content page b. the same logo in the same location on each content page c. a similar navigation area on each content page d. a different background color on each page
A ____ attack is a simple attack in which ICMP Echo Request packets are sent to a victim, who continues to send packets in response, effectively choking available bandwidth.
A. ping flood B. teardrop C. session hijacking D. buffer overflow
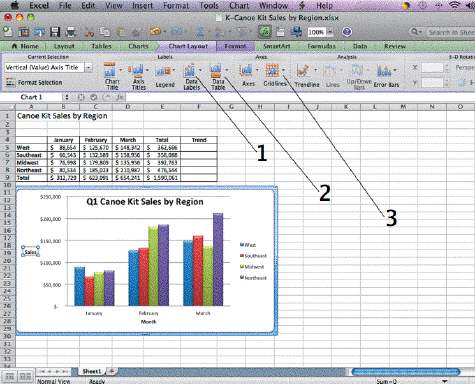 In the accompanying figure, Item 3 points to the Gridlines button, which you can use to enhance the visual appeal of the chart's ____.
In the accompanying figure, Item 3 points to the Gridlines button, which you can use to enhance the visual appeal of the chart's ____.
A. worksheet data B. axes C. data table D. plot area
A PivotTable is limited to a single table of data.
Answer the following statement true (T) or false (F)