The _________ contains field names and data values appended to a URL.
Fill in the blank(s) with the appropriate word(s).
query string
Computer Science & Information Technology
You might also like to view...
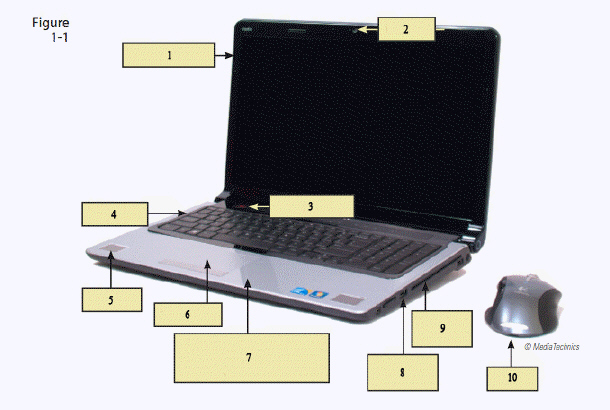 In the figure above, item 1 is pointing to the ____.
In the figure above, item 1 is pointing to the ____.
A. touchpad B. CD/DVD drive C. display device D. hard disk drive
Computer Science & Information Technology
What type of malware consists of a set of software tools used by an attacker to hide the actions or presence of other types of malicious software, such as a virus?
A. rootkit B. backdoor C. wrapper D. shield
Computer Science & Information Technology
In SQL, the ____ symbol is used as a wildcard to represent any collection of characters.
A. * B. % C. ? D. !
Computer Science & Information Technology
Hybrid notebook-tablet computers are also called convertible tablets or ____.
A. 2-in-1 computers B. netbook computers C. laptop computers D. PDAs
Computer Science & Information Technology