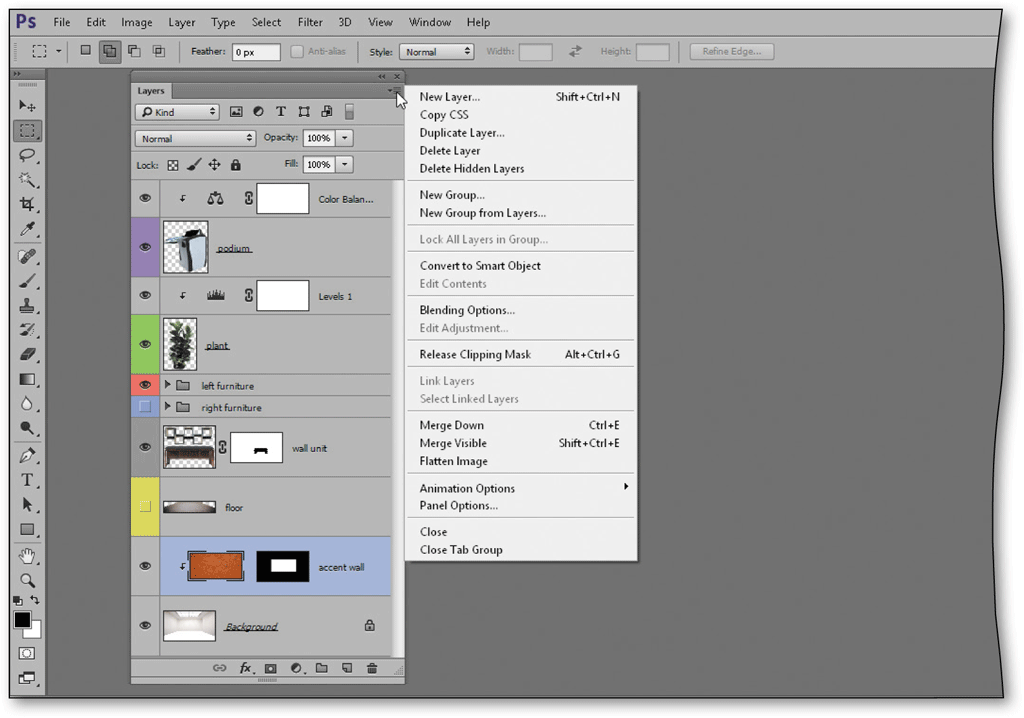
?
As shown in the accompanying figure, a hollow lock indicates that a layer is _____.
A. preset
B. transparent
C. fully locked
D. partially locked
Answer: D
You might also like to view...
Answer the following questions for the certification report shown here.
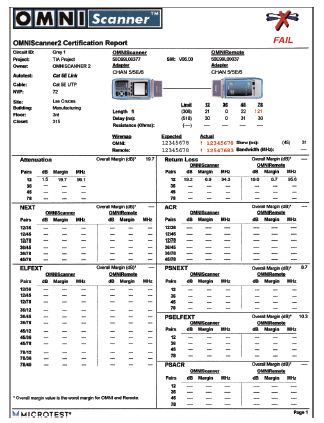
a. Why did the cable fail the test?
b. Draw the wiremap diagram for this cable.
The Merge & Center button is located in the ________
A) Alignment group on the HOME tab B) Styles group on the HOME tab C) Alignment group on the PAGE LAYOUT tab D) Styles group on the LAYOUT tab
Which of the following is an example of privilege escalation?
A. A hacker accesses a printer from the Internet, then the print server, and then the domain controller B. A hacker sends many oversized ping packets. C. A hacker convinces a user to reveal a password. D. A hacker follows a user into the facility.
The replacement operation combines removal and insertion into a single operation.
Answer the following statement true (T) or false (F)