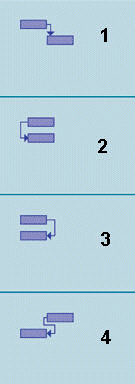
 The item marked 2 in the accompanying figure is a ____ task dependency.
The item marked 2 in the accompanying figure is a ____ task dependency.
A. Finish-to-Finish
B. Start-to-Finish
C. Finish-to-Start
D. Start-to-Start
Answer: D
You might also like to view...
Which of the following DoS attacks sends a UDP packet to a random port on the victim’s system?
A) SYN flood B) Ping of Death C) Smurf attack D) UDP flood
____ is the total amount of opposition to the flow of current and is measured in ohms.
A. Impedance B. Inductance C. Capacitance D. Conductance
Address Resolution Protocol (ARP) is a method by which the network layer (Layer 3) of the OSI is linked to the________ layer
a. Data link (Layer 2) b. Application (Layer 7) c. Physical (Layer 1) d. None of the above
Carol would like to implement a control that protects her organization from the momentary loss of power to the data center. Which control is most appropriate for her needs?
A. Redundant servers B. RAID C. UPS D. Generator