To send data securely to the server, you should use the get method.
Answer the following statement true (T) or false (F)
False
Computer Science & Information Technology
You might also like to view...
Unintentional _____________ occur in software and hardware because of failures in the development and sustainment process.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
All of the following are popular Web browsers today EXCEPT ________
A) Chrome B) Internet Explorer C) Safari D) Netscape
Computer Science & Information Technology
The aspect of a DoS attack that makes a server do a lot of processing and responding is called ____________________.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
Find the x- and y-intercepts of the equation and use them to sketch the graph. ![]()
A. 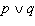 x-intercept
x-intercept ![]() , y-intercept
, y-intercept ![]()
B. 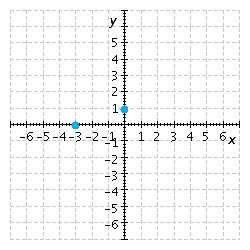 x-intercept
x-intercept ![]() , y-intercept
, y-intercept ![]()
C. 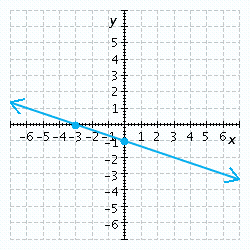 x-intercept
x-intercept ![]() , y-intercept
, y-intercept ![]()
D.  x-intercept
x-intercept ![]() , y-intercept
, y-intercept ![]()
E. 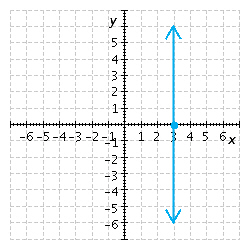 x-intercept
x-intercept ![]() , y-intercept none
, y-intercept none
Computer Science & Information Technology