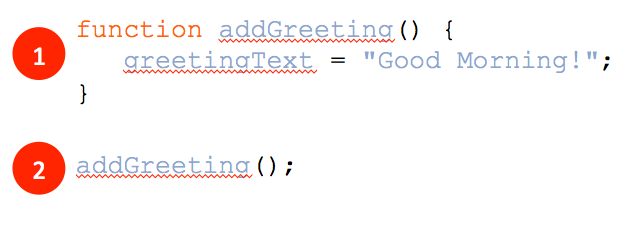
Referring to the figure above, what is the role of the three lines of code labeled with the number 1?
A. function call
B. event listener
C. function
D. conditional statement
Answer: C
You might also like to view...
Two families of elliptic curves are used in cryptographic applications: prime curves over Zp and __________ over GF(2m).
Fill in the blank(s) with the appropriate word(s).
How are full and differential database backups used?
A. a differential backup is followed by one or more full backups B. full backups copy data that has changed since the last differential backup C. differential backups are usually performed more often than full backups D. differential backups are more resource intensive than full backups
How many subnet bits are used for the IP address/mask 130.184.59.65/17?
A) 7 B) 5 C) 9 D) 1
The _______ in 1000BaseT means that twisted-pair cable is used
Fill in the blank(s) with correct word