The CISSP-ISSEP concentration focuses on the knowledge areas that are part of enterprise security management.
Answer the following statement true (T) or false (F)
False
You might also like to view...
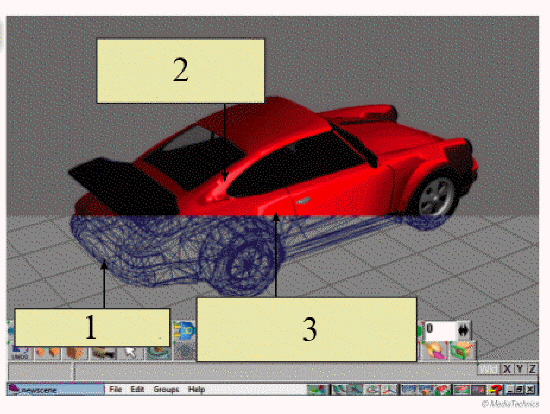 In the figure above, the drawing indicated by item 1 was created by ____.
In the figure above, the drawing indicated by item 1 was created by ____.
A. outlining every surface on the front, back, and inside of the object B. using the ray tracing feature C. sifting the image D. tracing an image of a car on a graphics tablet
You can configure an Apache Web server manually by editing configuration files in the ____ directory.
A. /etc/apache2/config B. /etc/apache2/ C. /etc/apache/files D. /etc/apache/config
The upper-left corner of the Welcome Screen contains links to sites where you can access additional information and tutorials.
Answer the following statement true (T) or false (F)
? Critical Thinking Questions Case 10-1 ? Sam has been asked to classify a number of different processing systems that his consultancy's client uses. Sam is analyzing a processing system and he has determined that it is an online processing system and not a batch processing system. Which of the following observations helped him determine the system??
A. ?The system allowing delays in transactions B. ?The system's tasks running on a predetermined schedule, without user involvement C. ?The system avoiding a constant dialog between the user and the system D. ?The system processing transactions completely when and where they occur