A ________ can be used to block unauthorized access to a network
A) filter
B) firewall
C) hub
D) switch
B
You might also like to view...
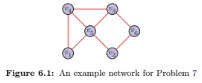
Consider an unweighted and undirected wireless network, as shown in Figure 6.18 in the text book (reproduced as Figure 6.1 of this solution manual). Identify the nodes with the highest wireless flow betweenness. What are the impacts on the resources of the nodes with high WFB?
Sort a file ‘data1’ and put the sorted file in a file called ‘data1.sorted’. Give the command that uses both input and output redirection.
What will be an ideal response?
In a(n) ____________________, there are thousands or millions of users simultaneously accessing dozens or hundreds of game servers across multiple communication channels.
Fill in the blank(s) with the appropriate word(s).
Highlights in the Vim editor remain from one session to the next, what specific term is used to describe these persistent highlights?
permanent gluey sticky