Estimate the time to complete each task of the task model produced in Exercise 14–6 and determine the critical path.
What will be an ideal response?
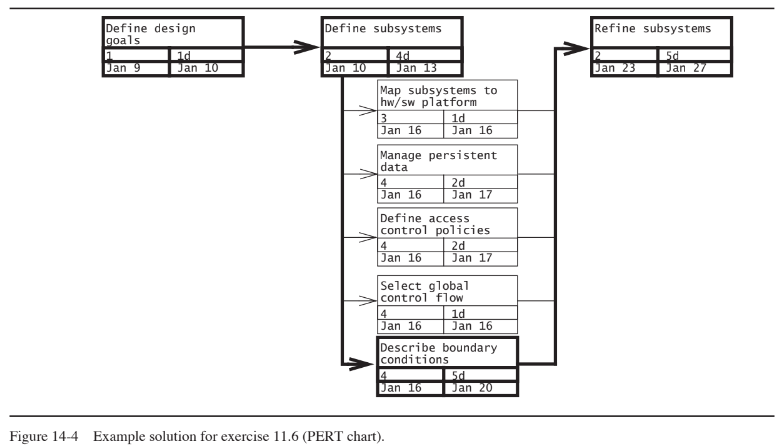
Note to the instructor: the estimates provided by the students need not (and will not) be realistic. The goal of the
exercise is to check the understanding of the concepts of critical path and task dependency. The example solution in
Figure 14-3 depicts the task model as a PERT chart and indicates the critical path in bold.
You might also like to view...
MC A difference between recursion and iteration is that:
a) iteration involves an explicit repetition structure unlike recursion. b) recursion is associated with a counter controlled repetition. c) iteration cannot execute infinitely, like recursion. d) None of the above.
When a code statement violates the macro rules established by Access, a(n) ____ error occurs.
A. event B. run-time C. syntax D. logic
Which of the following viruses creates a peer-to-peer botnet?
A) Zafi.d B) Shamoon C) Mirai D) Gameo ver ZeuS
Answer the following statements true (T) or false (F)
1) A tree node that has no children is called a None node. 2) Each link a tree node refers to is a child or a subtree of that node. 3) A stack is referred to as a LIFO data structure because it is a linear data structure. 4) The level-order traversal of a binary tree visits the nodes of the tree, starting at a leaf and progressing toward the root node level. 5) A sibling of a leaf in a tree can be a parent.