In the accompanying figureofa Microsoft Access 2016 document, the symbol that Box 1 is pointing to appears when you:?
?
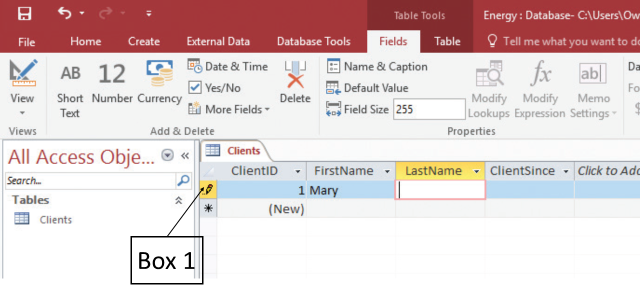
A. ?select the primary key value.
B. ?delete a record.
C. ?start typing a value in a field.
D. ?modify the foreign key value.
Answer: C
You might also like to view...
____________ is a free programming environment that is available for download from the Microsoft Web site.
a. Visual Studio 2015 Community Edition b. Visual Studio 2015 Professional c. The MSDN library d. Internet Explorer
Describe the two IPSec modes of operation.
What will be an ideal response?
____________________ is a technique used to gain unauthorized access to computers, wherein the intruder sends messages whose IP addresses indicate to the recipient that the messages are coming from a trusted host.
Fill in the blank(s) with the appropriate word(s).
What terms does Cisco use to differentiate between the two types of ports implemented at Layer 2 or Layer 3 on a multilayer switch?
What will be an ideal response?