Explain how general controls impact transaction integrity and the financial reporting process.
What will be an ideal response?
Consider an organization with poor database security controls. In such a situation, even data processed by systems with adequate built in application controls may be at risk. An individual who can circumvent database security, may then change, steal, or corrupt stored transaction data. Thus, general controls are needed to support the functioning of application controls, and both are needed to ensure accurate financial reporting.
PTS: 1
You might also like to view...
Answer the following statements true (T) or false (F)
1) An interface cannot declare any instance variables. 2) Establishing the relationship between a listener and the component it listens to is accomplished using polymorphism. 3) A reference variable can refer to an object of a child class, but not any further down the inheritance hierarchy. 4) Polymorphism via inheritance requires that all classes in the inheritance hierarchy are concrete. 5) An interface name may be used as a reference type.
What do slowly changing dimensions (SCDs) represent to a database designed for decision-support?
What will be an ideal response?
Consider the following database schema:
1. Supplier(SName, ItemName, Price)—supplier SName sells item ItemName at Price
2. Customer(CName, Address)—customer CName lives at Address.
3. Order(CName, SName, ItemName, Qty)—customer CName has ordered Qty of item ItemName from supplier SName.
4. Item(ItemName, Description)—information about items.
(a) Draw the E-R diagram from which the above schema might have been derived. Specify the keys.
(b) Suppose now that you want to add the following constraint to this diagram: Every item is supplied by some supplier . Modify the diagram to accommodate this constraint. Also show how this new diagram can be translated back to the relational model.
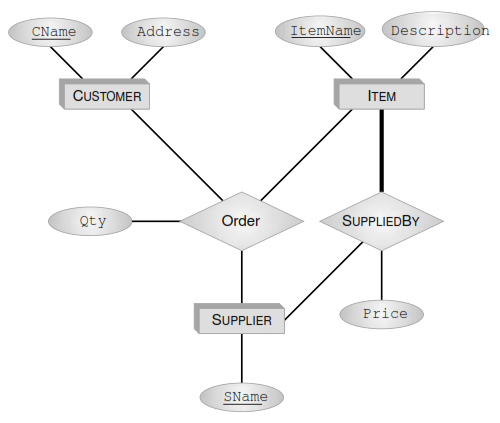
(c) Repeat parts (a) and (b) in UML.
What are swap partitions and how are they used?
What will be an ideal response?