The analysis of multi-event patterns is called ________.
A. event scoring
B. event correlation
C. event aggregation
D. event filtering
B. event correlation
You might also like to view...
Transaction processing enables a program to ________ or ________ a transaction based on whether the transaction was successful.
a. save, delete b. commit, rollback c. save, rollback d. commit, delete
Explain the procedures and techniques needed to achieve a conceptual data model.
What will be an ideal response?
Answer the following statements true (T) or false (F)
1. Strategic managers work in a highly uncertain decision-making environment. 2. Operations managers most often make one-time decisions but the decisions made by strategic managers tend to be repetitive. 3. Middle managers are highly dependent on external information. 4. Strategic managers tend to use information that is more current than information used by middle managers. 5. Often, considering organizational subcultures is more useful than is considering organizational culture.
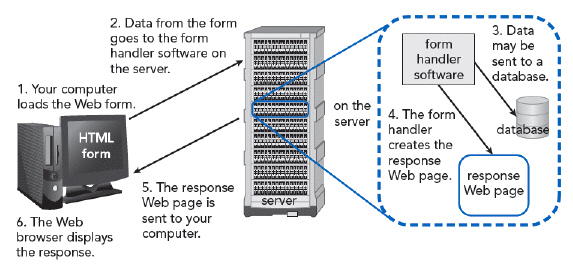 All of the following are examples of database software that can be used to store and manipulate data in the situation shown in the accompanying figure EXCEPT ____.
All of the following are examples of database software that can be used to store and manipulate data in the situation shown in the accompanying figure EXCEPT ____.
A. PHP B. MySQL C. MS SQL D. Oracle