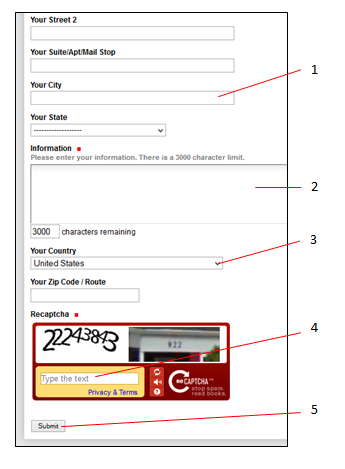
In the figure above, which number refers to the security challenge?
A. 1
B. 2
C. 3
D. 4
Answer: D
Computer Science & Information Technology
You might also like to view...
Write a C++ program fragment that will read a line of text and echo the line with all uppercase letters deleted. Declare variables and include necessary header.
What will be an ideal response?
Computer Science & Information Technology
____ is the transfer of live transactions to an off-site facility.
A. Electronic vaulting B. Server clustering C. Bare metal recovery D. Remote journaling
Computer Science & Information Technology
What is a computer that is controlled by a master, and used to launch various types of attacks?
a. bot b. bug c. cluster
Computer Science & Information Technology
A(n) ________ SmartArt object is used display how parts relate to the whole
Fill in the blank(s) with correct word
Computer Science & Information Technology