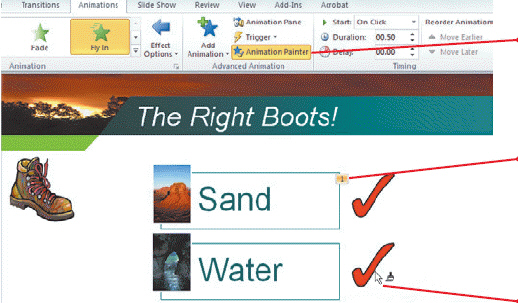
 The Animation Painter in the accompanying figure is used to transfer the animation and its custom settings to any other ____________________ in any open presentation.
The Animation Painter in the accompanying figure is used to transfer the animation and its custom settings to any other ____________________ in any open presentation.
Fill in the blank(s) with the appropriate word(s).
object
Computer Science & Information Technology
You might also like to view...
A(n) ________ is an attack in which multiple systems are used to flood servers or network devices or links with traffic in an attempt to overwhelm its available resources, making it unavailable to respond to legitimate users.
A) DDoS B) DoS C) ODC D) SAL
Computer Science & Information Technology
________ jobs in a multiprogramming computer system mainly use peripheral devices to perform their tasks.
a) processor-bound b) compute-bound c) I/O-bound d) none of the above
Computer Science & Information Technology
Why is it important to add elements and styles to charts such as titles, legends, and labels?
What will be an ideal response?
Computer Science & Information Technology
The command to renew an IPv6 address that was issued by a DHCP server is________
Fill in the blank(s) with correct word
Computer Science & Information Technology