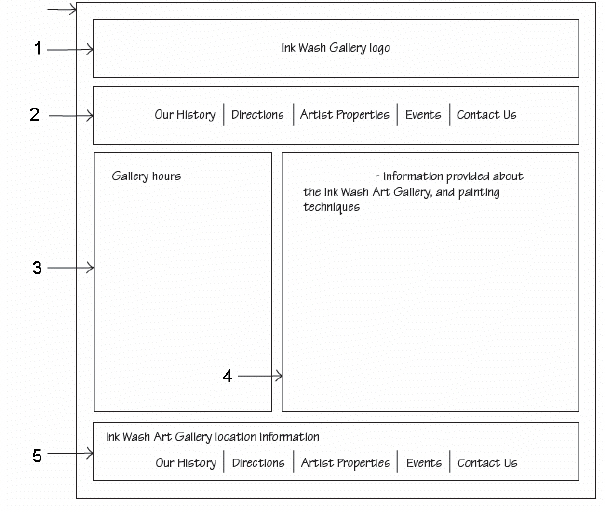
 The box marked 5 in the accompanying figure is a ____.
The box marked 5 in the accompanying figure is a ____.
A. bottom bar
B. nav
C. "contact us" bar
D. footer
Answer: D
Computer Science & Information Technology
You might also like to view...
Define each of the following security terms and give an example of how it is used.
a) secret key cryptography b) public key cryptography c) digital signature d) digital certificate e) hash function f) SSL g) Kerberos h) firewall
Computer Science & Information Technology
LinkedIn lets you send only text messages to other members
Indicate whether the statement is true or false
Computer Science & Information Technology
What’s rendering?
What will be an ideal response?
Computer Science & Information Technology
In the weighted point evaluation method, if a product receives a vendor support score of 80 and the weight of the vendor support criterion is 10%, the product gets a weighted score of ____ points for vendor support.
A. 8 B. 10 C. 80 D. 800
Computer Science & Information Technology