The threat evaluation process performed when designing a business continuity plan (BCP) or disaster recovery plan (DRP) evaluates risk in light of work process and is similar in nature to the technique used when designing security policies. What is this threat evaluation process called?
A Business impact analysis
B Quantitative analysis
C Qualitative analysis
D Threat modeling
Answer: A Business impact analysis
You might also like to view...
Suppose a memory manager has chosen a modified page for replacement. This page must be sent to secondary storage before the new page may be placed in its page frame. Therefore, the memory manager requests an I/O operation to write this page to secondary storage.An entry is made in a list of I/O requests waiting to be serviced. Thus the page will remain in main memory for some time before the requested I/O operation is performed. Now suppose that, while the other I/O requests are serviced, a running process requests the page to be replaced.How should the memory manager react?
What will be an ideal response?
The Debug button will return you to the MS VBA Editor window, and the line of code that contains the error will be highlighted in which of the following colors?
A) Yellow B) Orange C) Red D) Blue
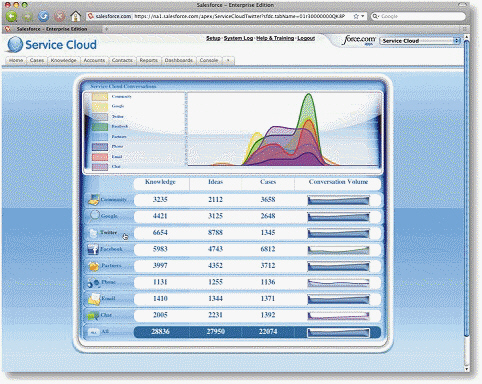 The Salesforce Service Cloud, seen in the accompanying figure, is a business application that runs in the Cloud.
The Salesforce Service Cloud, seen in the accompanying figure, is a business application that runs in the Cloud.
Answer the following statement true (T) or false (F)
Which of the following numeric data types is used for smaller, less precise floating-point numbers?
A. Double B. Float C. Short D. Byte