A rootkit is a piece of software that masquerades as an innocent, and perhaps useful, program, but that is actually designed for malicious purpose.
Answer the following statement true (T) or false (F)
False
False. A Trojan horse is a piece of software that masquerades as an innocent program, and a rootkit is a program that embeds itself into a computer's operating system and acquires special privileges that would normally be available to the operating system.
You might also like to view...
The most general class in a class hierarchy is placed at the bottom of the hierarchy.
Answer the following statement true (T) or false (F)
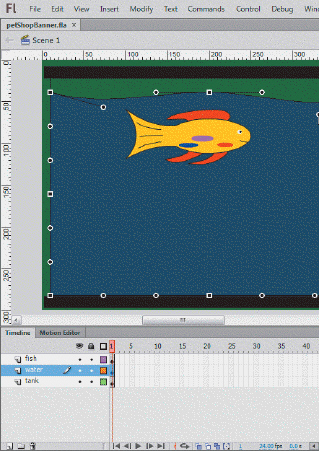 Referring to the accompanying figure, ____ handles are circles.
Referring to the accompanying figure, ____ handles are circles.
A. envelope B. free transform C. tangent D. rotation
Your network address is 192.168.100.0. What prefix allows you to assign 30 host addresses?
A. /29 B. /30 C. /27 D. /28
Define non-process inks.
What will be an ideal response?