If an entity's content is found within the DTD, the entity is known as a(n) _____ entity.
A. internal
B. persistent
C. contained
D. consistent
Answer: A
You might also like to view...
The ____ is the person responsible for the definition and deployment of all defense strategies, defense-in-depth schemes, and authorization functions for the protected, physical space.
A. digital forensics professional B. physical security professional C. enterprise continuity professional D. security architect
A(n) _____ is a data validation rule that can be used for data items that must have certain values.
A. existence check B. validity check C. batch check D. reasonableness check
Suppose Intel did not develop the first microprocessor. Was the microprocessor inevitable?
What will be an ideal response?What will be an ideal response?
What is the least number of degrees that you could rotate an equilateral triangle (3 equal sides) around its center so that it appears to be unchanged? 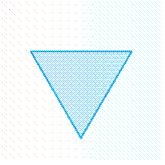 The answer is
The answer is ![]() .
.
Fill in the blank(s) with the appropriate word(s).