____ dictates the assumptions and underlying conditions that apply to that specific security setting.
A. Context
B. Content
C. Risk
D. Scope
Answer: A
Computer Science & Information Technology
You might also like to view...
The _________ accepts requests for access and configuration from a client and enforces the lock on the underlying resource.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
What is the catch or declare rule?
What will be an ideal response?
Computer Science & Information Technology
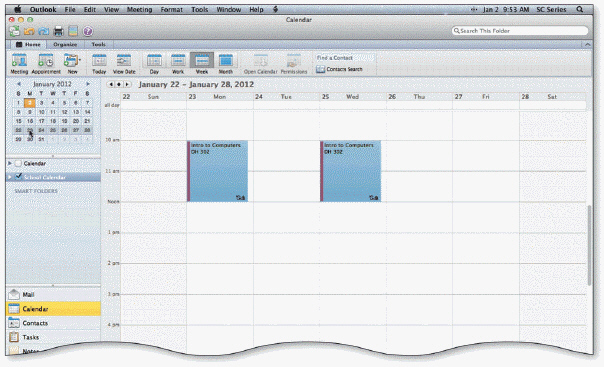 In the accompanying figure, the purple bars indicate a(n) tentative appointment.
In the accompanying figure, the purple bars indicate a(n) tentative appointment.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
When setting up a mail merge document to prepare the envelopes for a set of merged letters, select ____ as the type of document.
A. Directory B. Envelopes C. Labels D. Letters
Computer Science & Information Technology