What type of message authentication code uses hashing to authenticate the sender by using both a hash function and a secret cryptographic key?
A. SHA-384
B. HMAC
C. RIPEMD
D. MD5
Answer: B
You might also like to view...
Which of the following statements is true?
a. Strings can be used in a switch statement’s controlling expression and in its case labels. b. Strings can be used in a switch statement’s controlling expression but not in its case labels. c. Strings cannot be used in a switch statement’s controlling expression but can be used in its case labels. d. Strings cannot be used in a switch statement’s controlling expression and cannot be used in its case labels.
An __________ is a server computer that negotiates the use of a specific EAP method with an EAP peer, validates the EAP peer’s credentials, and authorizes access to the network.
Fill in the blank(s) with the appropriate word(s).
Connection-oriented, concurrent server.
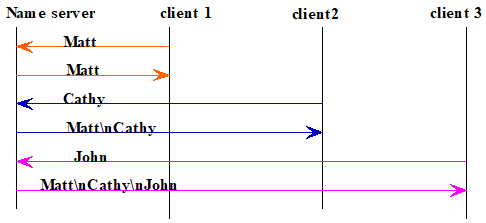
Using the three-tier software architecture presented in this chapter, design and implement a client-server suite for the following protocol (it is not a well-known service): Each client sends to the server a name. The server accumulates the names received from successive clients (by appending each, with a linefeed (‘
’), to a static string). Upon receiving a name, the server sends the names that it has collected to the client. The figure below illustrates the sequence diagram of a session of the protocol.
Ethical decisions need to be made whenever a business practice or product is legal or socially acceptable in one country but not in another. One example is ____.
A. copyright law B. religion C. vaporware D. corporate missions