A ____ constantly monitors the radio frequency (using wireless probes) for attacks.
A. wireless intrusion detection system (WIDS)
B. wireless AP detection system (WADS)
C. rogue AP prevention system (RAPS)
D. rogue AP detection system (RADS)
Answer: A
You might also like to view...
You could use ________ technology to connect your smartphone to a wireless headset
Fill in the blank(s) with correct word
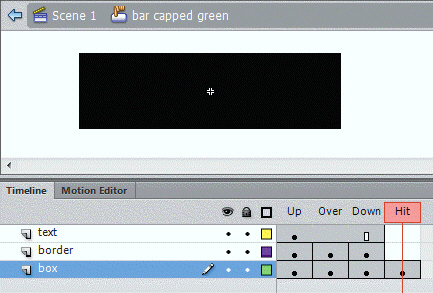 The item across the bottom of the accompanying figure is the ____________________ timeline.
The item across the bottom of the accompanying figure is the ____________________ timeline.
Fill in the blank(s) with the appropriate word(s).
The FV function has two optional arguments, ________ and ________
A) pv; rate B) pv; type C) rate; payment D) payment; type
? Critical Thinking Questions Case 9-2 ? Emily is functioning with her customer, Anna, on the design of a new database. She describes to Anna that key fields are utilized to access, coordinate, and preserve the data records. ?Emily tells Anna that a primary key is a field or combination of fields that individually and minimally recognizes a specific entity. She mentions that there may be an option of fields or field combinations to use as the primary key. Which of the following is the term used for a feasible primary key?
A. ?Candidate key B. ?Ancillary key C. ?Foreign key D. ?Multifaceted key